Composition analysis of applications
How Binary Composition Analysis (BCA) enhances the security of your software: SBOM, vulnerability identification and regulatory compliance.
Strengthen Your Application Security
In today’s digital landscape, where software is omnipresent and increasingly complex, cybersecurity has become a critical concern.
Binary Composition Analysis (BCA), by generating a comprehensive Software Bill of Materials (SBOM) for applications, plays a key role in enhancing software supply chain transparency and reducing security risks.
Binary Composition Analysis (BCA), by generating a comprehensive Software Bill of Materials (SBOM) for applications, plays a key role in enhancing software supply chain transparency and reducing security risks.
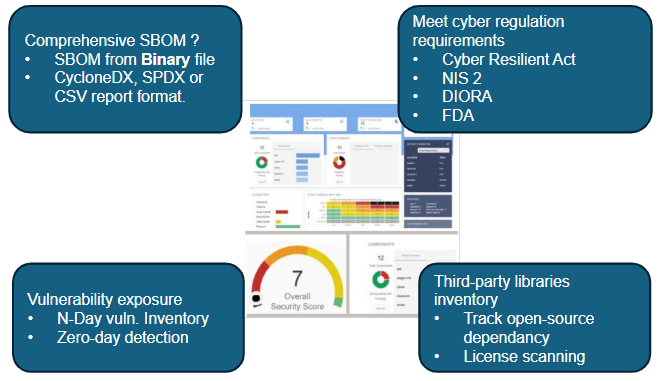
What is an SBOM?
- A comprehensive list of all software components, including open source and third-party libraries, used in an application.
- Benefits: Fast vulnerability identification and visibility into dependencies.
- Importance: Helps manage security risks, facilitates application maintenance, and reduces regulatory non-compliance risks.
- Key Steps:
1. SBOM Generation: Code analysis to identify all software components used in the application.
2. Vulnerability Management (N-Days): Identification of known vulnerabilities within detected components.
3. License Management: Identification of open-source license types associated with the components.
Our 5-Step Analysis Process
1. Needs Assessment: Together with our sales team, we define the scope and depth of the analysis based on your requirements.
2. Application Submission: You securely provide us with the binary or executable file to be analysed.
3. Technical Analysis: Our experts perform an in-depth Binary Composition Analysis (BCA) of your application.
4. Report Generation: The report includes, upon request:
5. Report Delivery: you will receive the report in the format of your choice: CycloneDX, SPDX, or CSV
2. Application Submission: You securely provide us with the binary or executable file to be analysed.
3. Technical Analysis: Our experts perform an in-depth Binary Composition Analysis (BCA) of your application.
4. Report Generation: The report includes, upon request:
- The SBOM (Software Bill of Materials)
- Open source components licenses
- Identified vulnerabilities
5. Report Delivery: you will receive the report in the format of your choice: CycloneDX, SPDX, or CSV
Why Perform Binary Composition Analysis?
- Ensure Compliance and Transparency: Regulations and industry standards increasingly demand full visibility into software composition. A Software Bill of Materials (SBOM) offers clear, structured documentation—making compliance easier and more efficient.
- Strengthen Supply Chain Security:The software supply chain is a growing target for cyber threats. An SBOM helps identify compromised or unauthorized components, enhancing security at every stage of the development lifecycle.
- Simplify Maintenance and Updates: With a complete inventory of all components and their dependencies, an SBOM makes it easier to track versions, apply updates, and manage long-term software maintenance.